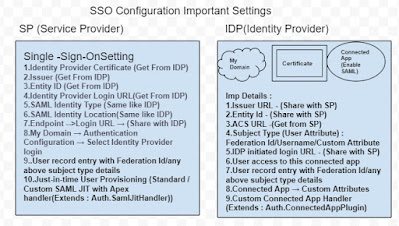
If the User present in IDP and not present in SP ,What happens ?
With the unique identifier it will set up user account in SP, In Salesforce have option of "Enable Just-in-Time user provisioning" .For more details refer.
Ex: User Name / Email / Federation Id (Employee Id /Unique User Name) /User Id
Note : Except the unique identifier, It will not share any other information from IDP to SP due to security reasons.
Explain Just-in-time User Provisioning in Salesforce Single Sign-On Settings?
Use Cases : With out creating the users in advance ,Create on the fly when SSO triggered.
- Salesforce Community user creation on the fly
- In Enterprise Org the user is part AD(Active Directory) group and SSO enabled for Org then in Salesforce Application can add JIT user provisioning standard & Share the user record expected attribute details to IDP.
- Okta is set up in any org to manage access across any application
Steps :
1.From IDP send the required user attributes in SAML & SP reads the SAML and create the user with the received information.
Ex: Federation Id, User Name, User Profile Id.
Single Sign On VS Social Sign On ?
- We can say, Social Sign On is one use case of Single Sign On.
- Now a days in many apps/website we can see option to login with Social network (Facebook/LinkedIn/Gmail/GitHub).
- Few of them not required to have the service provider registered earlier based on the request details it will respond, Few of them are much required to connect with IDP in advance before sending the request.
- If you are building the new mobile app and Would like to have Social Sign On, Please verify few of them available for free and few of them are paid.
- This feature is much useful to avoid the password fatigue
- To have additional security use this with combination of multifactor authentication
OpenID Connect VS SAML ?